Wie funktionieren Verschlüsselungstechnologien?
Lesezeit: 6 mins | 30. August 2021

A secure encrypted cloud solution is essential for any business, but many are not exactly sure what the different encryption methods involve or mean.
Encryption generally refers to a method that converts plain text into unreadable characters using a key. The encrypted text can be decrypted again using the same key.
More and more data is being processed, stored, and transmitted digitally, which is why the reasons for secure encryption are increasing at the same time. The risks of data loss or misuse are well known. This article will describe common methods in more detail and illustrate them using various examples.
In general, there are different types of encryption technologies. These include:
1. Symmetric encryption
2. Asymmetric encryption
3. Hybrid encryption
Therefore, there are various methods that apply these encryption types.
4. RSA encryption
5. SSL and TLS
6. AES-256-bit encryption
7. End-to-end encryption
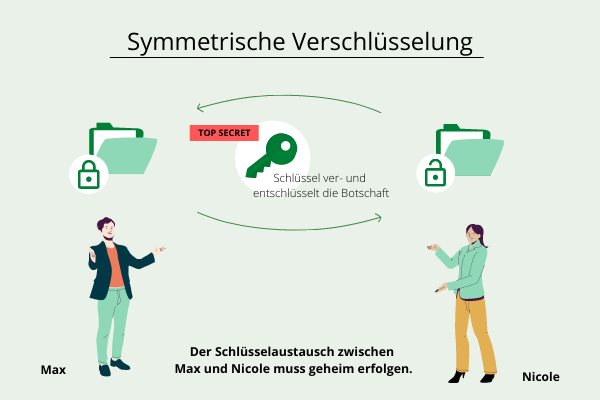
Symmetric Encryption
= also known as "secret key encryption"In symmetric encryption, only one key is needed for encryption and decryption. Therefore, the key must be known to both the sender and the receiver.
The advantages are that the method is considered simple and the exchange of messages is quick.
Disadvantages
Since the exchange of the key should be kept secret, the key exchange problem arises at this point. A secure way must be found to exchange the key. The safest way would be a personal meeting, which is often not practical.
If multiple messages are sent to different participants, the number of keys quickly increases.
Asymmetric Encryption
= also known as "public key encryption"
Asymmetric encryption requires two keys. The key for encryption is public and accessible to everyone, while the key for decryption is private.
Asymmetric encryption has the advantage of providing high security that cannot be easily cracked by attackers. This method can also bypass the key exchange problem or create digital signatures that serve for authentication.
More about digital signatures can be found in the section that discusses the RSA algorithm.
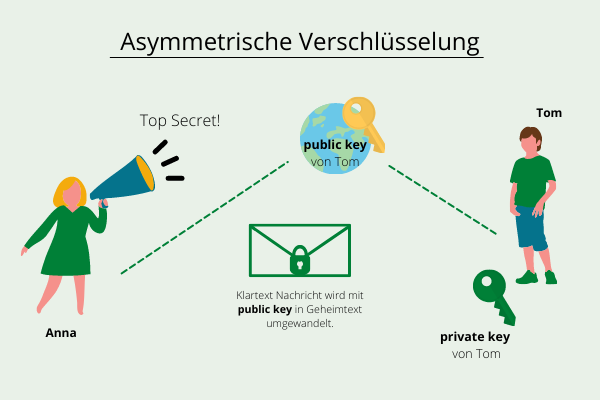
Asymmetric Encryption
Suppose Anna wants to send a secret message to Tom.
First, a key pair needs to be generated for Tom to exchange. Now, Anna needs the public key of Tom to encrypt the plaintext message, which fortunately is public and thus does not need to be communicated secretly.
With the public key, Anna can now encrypt the message to Tom, and Tom can decrypt it with his private key.
Disadvantages
Despite the high security offered by this method, it is very computationally intensive and complex, especially when encrypting large amounts of data.
Thus, the method is also much slower than the symmetric method.
Hybrid encryption is therefore recommended as a solution proposal.
The hybrid encryption
The hybrid encryption is a mix of both encryption methods. For example, a symmetric key is exchanged using the asymmetric encryption method, so that the actual communication takes place symmetrically.
This not only avoids the computationally intensive and slow asymmetric method, but also the key exchange problem.
Key pairs can be created, for example, using the Diffie Hellmann method. This method is based on mathematical calculations and information between communication partners.
RSA Encryption
The name RSA comes from the first letters of the surnames of the mathematicians who discovered the method.
This is one of the most commonly used asymmetric methods, which is used to encrypt and create digital signatures.
RSA has the properties that plaintext letters are not always the same ciphertext letters. It also consists of a key pair - the private key cannot be calculated from the public one.
This method is therefore considered secure, as there is currently no algorithm that can factorize a number larger than 789 bits into its prime factors. Modern RSA encryptions therefore have a minimum length of 3072 bits.
To decrypt an RSA system, additional information is required, which is only contained in the private key.
The private key consists of a one-way function, meaning that the function is easy to calculate but cannot be reversed. The required additional information makes it easy to perform the reversal again.
RSA Signatures
As mentioned earlier, the RSA procedure can be used to create a digital signature that serves to authenticate the sender.
Unlike with asymmetric encryption, the sender creates the digital signature of the message using their private key, so the recipient can verify the digital signature with the public key.
There are two types of signatures: universal and non-universal.
Universal Signature
The private key is used to create a signature that is attached to the transmitted message. If a third party intercepts the communication channel, they can also verify the sender's authentication.*
Non-Universal Signature
The digital signature is also encrypted with the recipient's public key, so only they can verify the authenticity of the sender.
*The authenticity of the sender does not necessarily need to be kept secret at this point.
SSL and TLS
SSL stands for "Secure Socket Layer" and describes the layers that the encryption protocol uses in the data exchange between two computers. The communication between them is encrypted and thus protected against access by third parties.
The main task of SSL is to give the WWW user the assurance that he or she is communicating securely with the server and to secure the protocol HTTP (= Hypertext Transfer Protocol). The URL is displayed as HTTPS when the website has been secured by an SSL certificate. It can also be recognized by a lock symbol displayed in the URL bar or by the bar turning green.
TLS = "Transport Layer Security" is the newer version of SSL, which offers higher security. Since SSL is still much better known than TLS nowadays, it is often still referred to as SSL or the double term SSL/TLS is used.
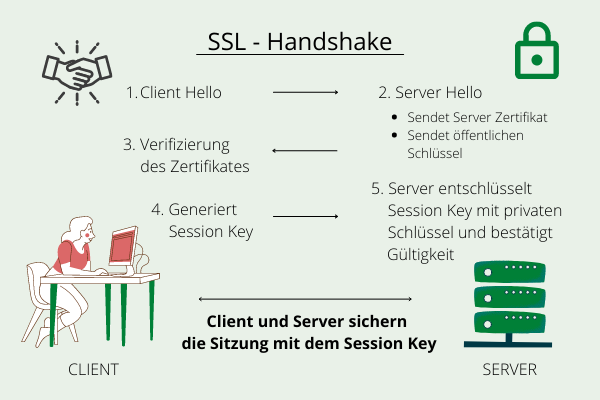
How does it work exactly?
SSL certificates authenticate the online identity and consist of a key pair and verified identification data. Certificates can be requested from a certification authority.
During a connection, the identity of the web server is requested, so a copy of the SSL certificate is sent to the requesting browser.
After the browser has verified the trustworthiness, the server can send back a digitally signed confirmation. If there is a match, an SSL encrypted session can now be initiated.
This process is called the "SSL handshake."
AES-256-Bit Encryption
The AES algorithm is a symmetric encryption method that uses only one key.
AES is a block cipher, and the block size depends on the key length. The length can be 128, 192, or 256 bits.
The predecessor DES = "Data Encryption Standard" was replaced by AES = "Advanced Encryption Standard" due to its short key length of 56 bits.
As computer processing power increased, DES was no longer able to provide sufficient security.
The special feature of this encryption technology is the transformation applied to each block.
The 4 Encryption Rounds
The encryption applies 4 different procedures to transform the blocks, and these procedures are applied repeatedly in multiple rounds.
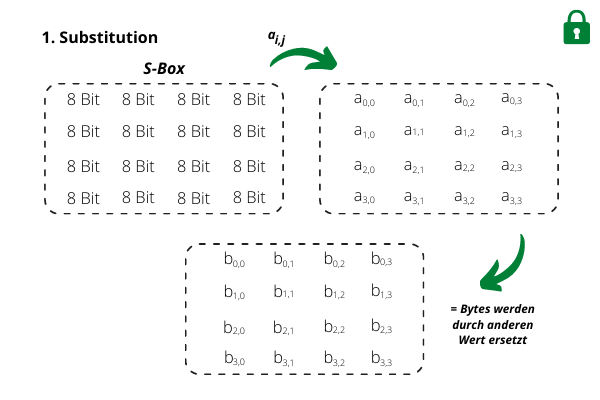
1. Substitution
Each byte is encrypted with a substitution box - a rule is given on which value a byte should be replaced with.2. Shift Row
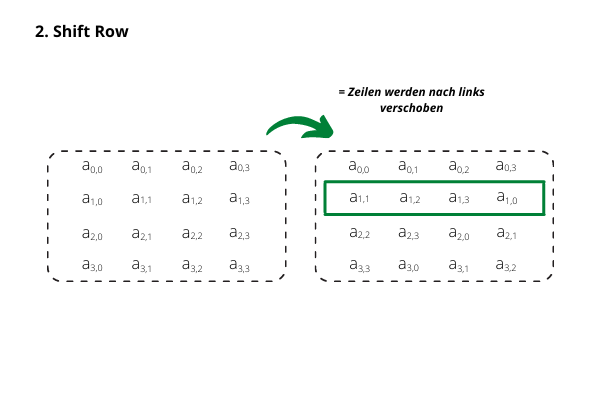
The rows of the table are shifted to the right by a certain number of columns - the overflowing cells are appended to the left.3. Mix Column
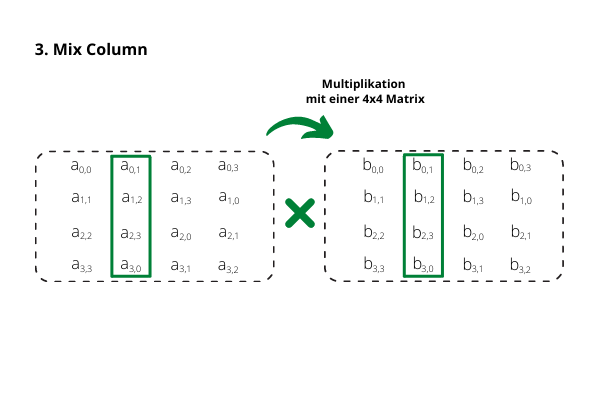
The columns are multiplied by a certain matrix - the bytes are seen as polynomials, not as numbers.4. Key Addition
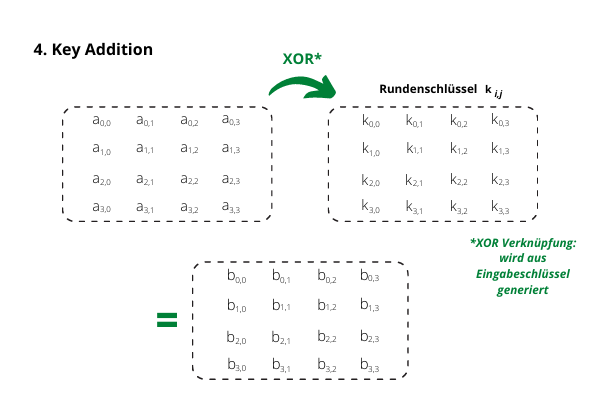
Each block is XORed with the current round key - the XOR operation is performed bit by bit.This process is applied in various areas, including data transfer using WLAN or VPNs, or in general data transfer.

Test leitzcloud as a secure cloud solution now
Secure your data in a securely encrypted cloud, with a sustainable data center in Germany.
Save your data securely now
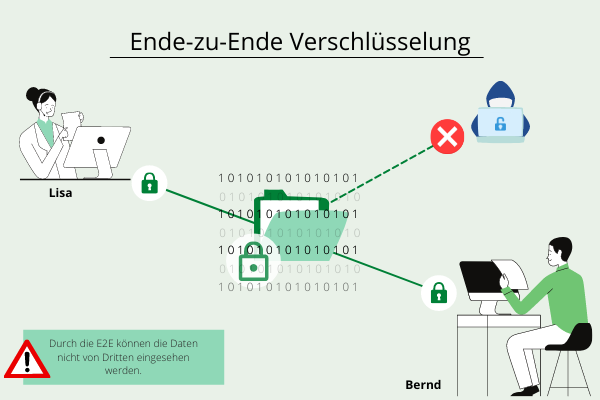
End-to-End Encryption
also known as "End-to-End-Encryption"End-to-End Encryption (E2EE) fully encrypts data between sender and receiver and can only be decrypted with the key of the desired recipient. The encryption and decryption process only takes place at the endpoints of the transmission.
How does it work?
E2EE uses several encryption techniques, usually employing hybrid encryption for key exchange.
The transmitted data is encoded using the symmetric AES-256 encryption and authenticated with the digital SSL certificate at the endpoints of communication.
For even more security, digital signatures can be added to the encryption to verify access authorization.
Advantages
E2EE promotes data privacy, as there is no access to personally identifiable information, while also preventing unwanted access to data exchange.
Furthermore, it is a secure method of communication since the key granting access is only known by the sender and receiver.
End-to-End Encryption with leitzcloud
Did you know that your data is also locally end-to-end encrypted with SafeSync?
Learn more about SafeSync
Sources:
Studyfix: Verschlüsselungsalgorithmen (accessed on August 22, 2021)
Boxcryptor: Encryption (accessed on August 24, 2021)
